At the recent MITRE ATT&CK conference, ATT&CKCon in Washington, leading MSSP Red Canary presented an interesting keynote presentation on how they advise organisations should use MITRE ATT&CK in cyber defence.
The first takeaway is: Don’t boil the ocean. Many organisations waste their time and efforts on vanity statistics, particularly when trying to map their detection and protective capabilities against all MITRE ATT&CK Techniques. In many respects, this is a fruitful exercise and at best, tells you little about your actual ability to detect and prevent adversarial behaviours. At worst, it can waste a lot of time and effort on focusing your cyber defence efforts in areas that will seldom or almost never be exploited by threat actors.
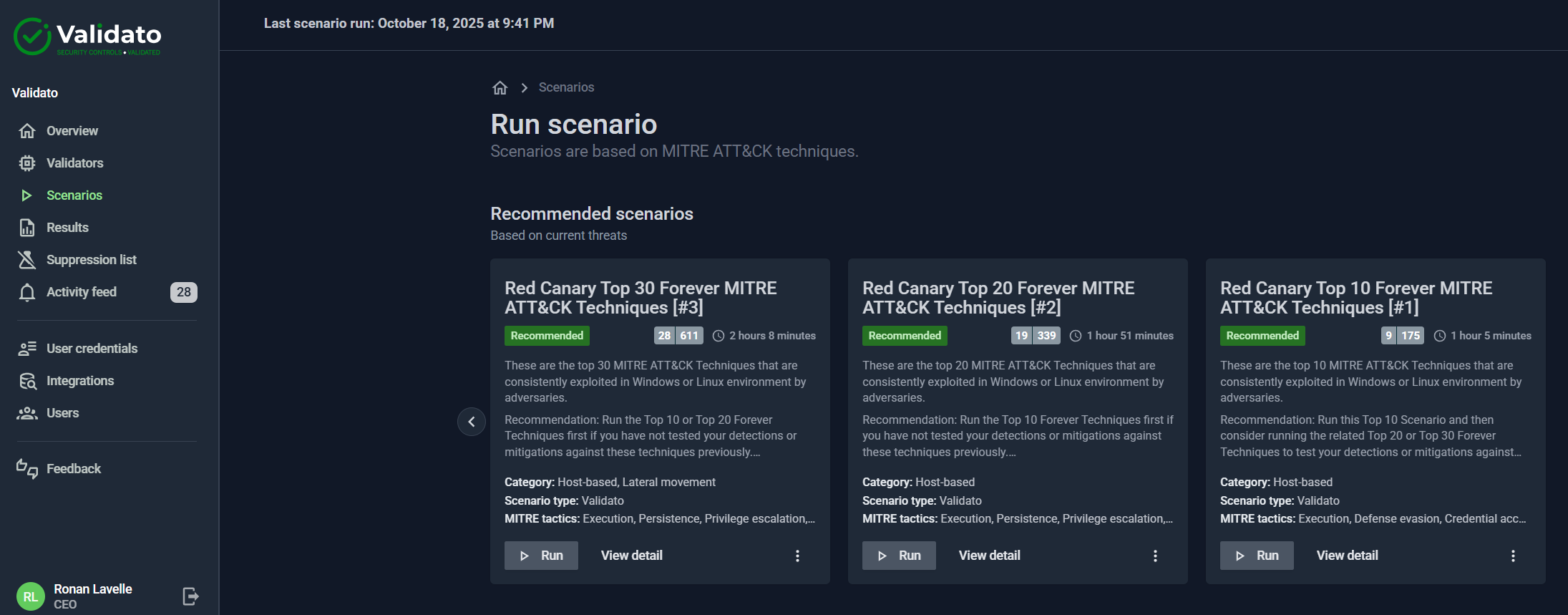
Red Canary has identified what they refer to as Forever Techniques. These are the most commonly exploited MITRE ATT&CK Techniques based on their observations as a managed security service provider.
Red Canary has created three Forever Techniques lists that map to the stage of maturity that your threat intelligence and cyber defence team is at today.
These are:
- Top 10 MITRE ATT&CK Forever Techniques (these are the absolute most exploited Windows and Linux functions that you should test first if you have not previously run attack simulation tests)
- Top 20 MITRE ATT&CK Forever Techniques (Once you have validated your security controls and ability to detect the top 10 techniques, this additional list of 10 Techniques is where your team should focus their efforts next)
- Top 30 MITRE ATT&CK Forever Techniques (Lastly, this list of the top 30 Forever Techniques encompasses the majority of the most commonly exploited Windows, Linux and Mac functions. If you have validated your controls and detection capabilities against all of these Techniques, you are going to be in a much better place to detect and fend off a wide range of cyber adversaries who will invariably attempt to use these ATT&CK Techniques).
This is about improving detections and visibility, but also preventative measures, through security control optimisation and strategic system hardening that disrupts adversaries’ ability to be successful.
So, what are the Top 10 MITRE ATT&CK Forever Techniques? They are:
- T1003 OS Credential Dumping
- T1027 Obfuscated Files or Information
- T1047 Windows Management Instrumentation
- T1055 Process Injection
- T1059 Command and Scripting Interpretor
- T1059.001 Powershell
- T1059.003 Windows Command Shell
- 1087.004 Cloud Accounts
- T1105 Ingress Tool Transfer
- T1218.011 Rundll32
Top 20 MITRE ATT&CK Forever Techniques:
- T1003 OS Credential Dumping
- T1003.001 LSASS Memory
- T1027 Obfuscated Files or Information
- T1036.003 Rename System Utilities
- T1036.005 Match Legitimate Name or Location
- T1047 Windows Management Instrumentation
- T1053.005 Scheduled Task
- T1055 Process Injection
- T1059 Command and Scripting Interpreter
- T1059.001 Powershell
- T1059.003 Windows Command Shell
- 1087.004 Cloud Accounts
- T1105 Ingress Tool Transfer
- T1112 Modify Registry
- T1114.003 Email Forwarding Rule
- T1218.005 Mshta
- T1218.011 Rundll32
- T1546.008 Accessibility Features
- T1569.002 Service Execution
- T1574.002 DLL Side-Loading
Top 30 MITRE ATT&CK Forever Techniques:
- T1003 OS Credential Dumping
- T1003.001 LSASS Memory
- T1027 Obfuscated Files or Information
- T1036 Masquerading
- T1036.003 Rename System Utilities
- T1036.005 Match Legitimate Name or Location
- T1047 Windows Management Instrumentation
- T1053.005 Scheduled Task
- T1055 Process Injection
- T1059 Command and Scripting Interpreter
- T1059.001 Powershell
- T1059.003 Windows Command Shell
- T1059.004 Unix Shell
- T1059.007 JavaScript
- T1078.002 Domain Accounts
- T1090 Proxy
- T1105 Ingress Tool Transfer
- T1112 Modify Registry
- T1114.003 Email Forwarding Rule
- T1218.005 Mshta
- T1218.010 Regsvr32
- T1218.011 Rundll32
- T1136.002 Domain Account
- T1546.008 Accessibility Features
- T1547.004 Winlogon Helper DLL
- T1562.001 Disable or Modify Tools
- T1564.008 Email Hiding Rules
- T1569.002 Service Execution
- T1574.002 DLL Side-Loading
- T1585.003 Cloud Accounts
While it might seem like a lot of work to devise appropriate tests to validate detections and protective capabilities, you need not worry. Validato customers can run these Red Canary scenarios in just three mouse clicks.
Reach out to the Validato team if you are interested in testing your detection and protection capabilities against Red Canary’s Forever Techniques.


