For modern organisations, the attack surface is not a static map but an ever-expanding, dynamic entity, reflecting the increasing complexity of our interconnected operations. In this volatile environment of escalating threats, relying on traditional, point-in-time security assessments is akin to navigating a storm with only a fleeting glimpse of the weather forecast – the picture is outdated almost as soon as it’s captured. To truly build and maintain cyber resilience, we must embrace a more dynamic, integrated, and proactive paradigm: the powerful synergy of Continuous Compliance and Security Posture Validation.
Continuous Compliance: Beyond the Audit, Towards a Living Security Culture
Continuous Compliance transcends the outdated model of periodic audits and rushed, checklist-driven preparations. It represents a fundamental shift towards embedding security and regulatory adherence into the very DNA of an organisation’s daily operations. This isn’t merely about achieving a compliant status at a specific moment; it’s about cultivating an ongoing state of readiness and vigilance. It means ensuring that crucial security controls are not only designed and implemented correctly but are also consistently functioning effectively, adapting to new threats, and evolving with the business.
The drive for continuous compliance stems from more than just regulatory pressure. It’s about building stakeholder trust, ensuring business continuity, protecting sensitive data, and maintaining a robust defense against the financial and reputational damage a breach can inflict. However, the journey to authentic continuous compliance requires more than internal policy and process; it demands tangible proof of control effectiveness in the face of real-world adversarial tactics.
Security Posture Validation: The Proving Ground for Your Defences
This is where Security Posture Validation, also known in some contexts as Adversarial Exposure Validation (AEV), steps into the spotlight. It is the proactive, empirical, and ongoing process of rigorously testing and validating the true effectiveness of an organisation’s security controls against the backdrop of realistic, contemporary cyber threats. Security Posture Validation moves decisively beyond theoretical assessments, vulnerability scans, or compliance checklists. It actively simulates sophisticated attack scenarios, mimicking the tactics, techniques, and procedures (TTPs) of real-world adversaries to provide an unvarnished view of how defences perform under pressure.
Imagine your security infrastructure as a fortress. Security Posture Validation doesn’t just review the blueprints (policies) or count the sentries (implemented controls); it actively tests the walls, gates, and surveillance systems against simulated siege engines and infiltration tactics. This continuous feedback loop identifies hidden weaknesses, misconfigurations, and critical vulnerabilities in real-time, allowing for prioritised remediation before attackers can exploit them.
The Unbreakable Bond: How Security Posture Validation Fuels Continuous Compliance (and Vice-Versa)
At Validato, we assert that these two pillars – Continuous Compliance and Security Posture Validation – are not just complementary, but inextricably and mutually beneficially linked. True, sustainable continuous compliance in today’s sophisticated threat landscape is simply unattainable without the dynamic, evidence-based insights furnished by continuous Security Posture Validation. Conversely, a robust compliance framework provides the strategic direction and impetus for more focused and effective validation efforts.
Consider the powerful interplay:
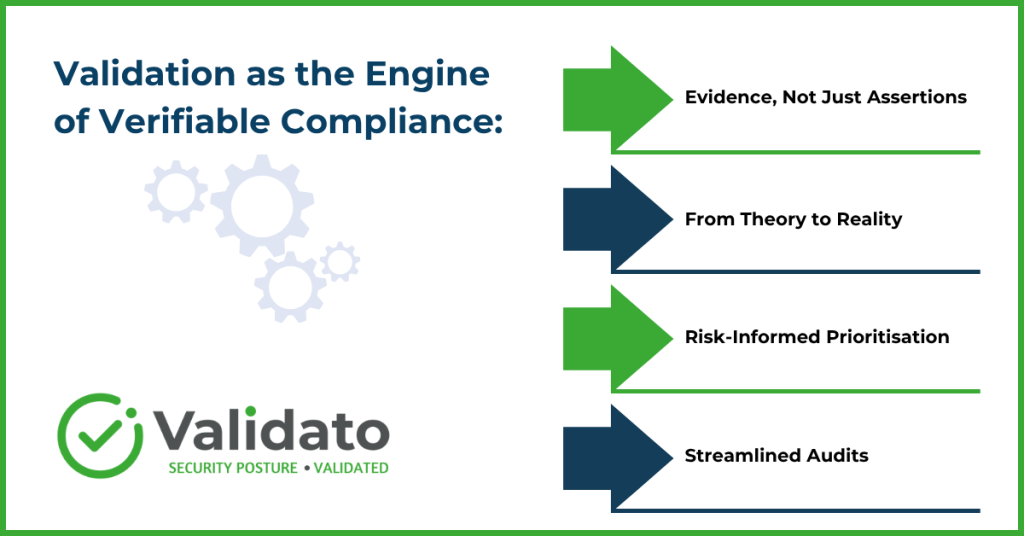
1. Validation as the Engine of Verifiable Compliance:
-
- Evidence, Not Just Assertions: Security Posture Validation provides the concrete, empirical evidence that security controls are functioning as intended. This allows organisations to demonstrate compliance, rather than merely claiming it, satisfying auditors and regulators with verifiable proof.
- From Theory to Reality: It translates theoretical compliance requirements into practical, validated security outcomes. A policy might dictate endpoint protection, but validation confirms if that protection can actually stop a modern Ransomware variant.
- Risk-Informed Prioritisation: By uncovering exploitable vulnerabilities, validation helps prioritise remediation efforts directly tied to compliance gaps, ensuring resources are focused on the most critical areas.
- Streamlined Audits: With a repository of continuous validation data, audit preparations become less burdensome and more about showcasing an ongoing, mature security program.
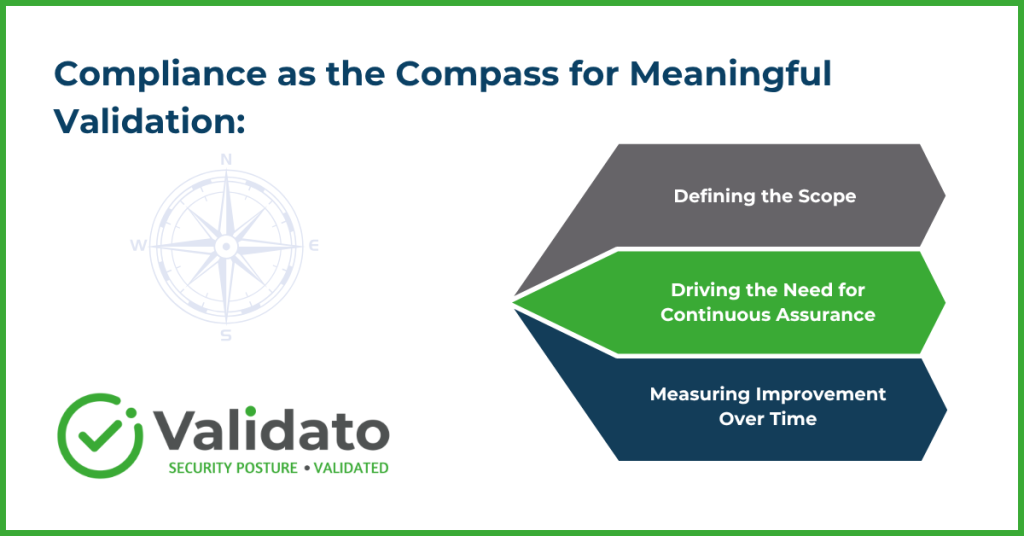
2. Compliance as the Compass for Meaningful Validation:
-
- Defining the Scope: Compliance frameworks (like ISO 27001, SOC 2, HIPAA, etc.) help define the critical assets and controls that require validation, ensuring efforts are aligned with regulatory obligations and business risk.
- Driving the Need for Continuous Assurance: The core principle of “continuous” in compliance necessitates ongoing proof of effectiveness, a need directly met by Continuous Security Posture Validation.
- Measuring Improvement Over Time: Validation provides the metrics to track how Security Posture—and therefore compliance adherence—improves over time in response to remediation and changing threats.
By leveraging Security Posture Validation to continuously test defences across crucial environments – such as Microsoft Windows, Linux, and Apple Mac endpoints – identifying and mitigating risks associated with over-privileged users, and rigorously testing the efficacy of pivotal security solutions like EDR/XDR platforms, organisations gain the actionable intelligence essential for both. This data is the bedrock of a resilient security posture and the demonstrable proof required for ongoing compliance.
Let’s revisit the analogy: a vehicle might pass its annual inspection (point-in-time audit), declaring it roadworthy. Continuous Compliance is akin to the regular, disciplined maintenance schedule – oil changes, tire checks, brake fluid top-ups – designed to keep the car in good running order. Security Posture Validation, then, is the equivalent of periodically taking that car to a closed track to perform simulated emergency braking maneuvers, evasive steering tests under adverse conditions, and acceleration trials. It’s about ensuring the car not only should be safe based on its maintenance but actually performs safely and reliably when truly tested. Both the regular maintenance (compliance) and the stress-testing (validation) are crucial for true, ongoing road-worthiness (security).

Meeting the Demands of Modern Cyber Resilience Mandates
The evolving regulatory landscape, with directives such as DORA (Digital Operational Resilience Act), NIS2 (Network and Information Security Directive), and the proposed UK Cyber Security & Resilience Act, underscores this imperative. These regulations are shifting the focus from static, audit-based compliance to a more demanding standard of demonstrable, ongoing operational resilience. They implicitly, and increasingly explicitly, call for organisations to continuously prove their defences can withstand modern cyber attacks. This level of assurance can only be achieved when continuous compliance is underpinned by robust, Continuous Security Posture Validation.
Validato: Empowering Your Journey to Integrated Security and Compliance
At Validato, we empower organisations to transform this symbiotic relationship from theory into operational reality. Our platform provides the advanced capabilities to continuously simulate adversarial behaviors, test control effectiveness across your diverse technology stack, and provide the clear, actionable intelligence needed to proactively strengthen defences. This validation-driven approach doesn’t just help you find and fix weaknesses; it provides the essential evidence stream to confidently maintain a resilient security posture and demonstrate unwavering, ongoing compliance.
In conclusion, the path to enduring cyber resilience is paved not by treating security validation and compliance as separate endeavors, but by recognising and cultivating their profound interdependence. By embracing this integrated approach, organisations can move beyond the limitations of outdated assessments and forge a truly proactive, adaptive, and verifiable security stance fit for the challenges of today and tomorrow.
Contact Validato for more information on Continuous Compliance and Security Posture Validation.


