Adversarial Exposure is redefining how organisations approach cybersecurity. By providing continuous validation to help achieve true cyber resilience. The imperative for modern businesses is clear: it’s no longer if you will face a cyber incident, but when. This reality has elevated the concept of Cyber Resilience from a buzzword to a fundamental operational requirement. Resilience, at its core, is the ability for an organisation to anticipate, withstand, recover from, and adapt to adverse conditions, stresses, and attacks on its cyber environment. Continue reading to learn more about achieving cyber resilience with adversarial exposure validation.
Many organisations mistakenly treat resilience as a post-incident aspiration. They pour millions into security solutions yet rely on outdated, episodic testing method. Such as, annual penetration tests or quarterly vulnerability scans. This practice is akin to a comprehensive security check-up that’s rendered obsolete the moment the report is printed.
The truth is that threat actors operate continuously. They don’t respect your quarterly budget cycles or wait for your next scheduled test. To meet this non-stop, dynamic challenge, security teams must evolve from reactive verification to proactive, continuous assurance by embracing Adversarial Exposure Validation (AEV).
The Critical Flaw in Point-in-Time Security: Why Traditional Methods Fail
Traditional security testing methods, while having their place, create a critical and often fatal time-gap vulnerability that compromises true cyber resilience.
- Vulnerability Scanning is necessary, but it only tells you if you have a known flaw. It offers no evidence of whether your multi-layered defences [firewall, cloud policies, EDR (Endpoint Detection and Response) , or SIEM (Security Information and Event Management)] will actually block or detect an attacker exploiting that flaw. This leaves a massive detection-validation gap.
- Penetration Testing provides deep, human-driven insight. But fundamentally represents a single, static snapshot of your environment. The findings are often obsolete within weeks due to factors like:
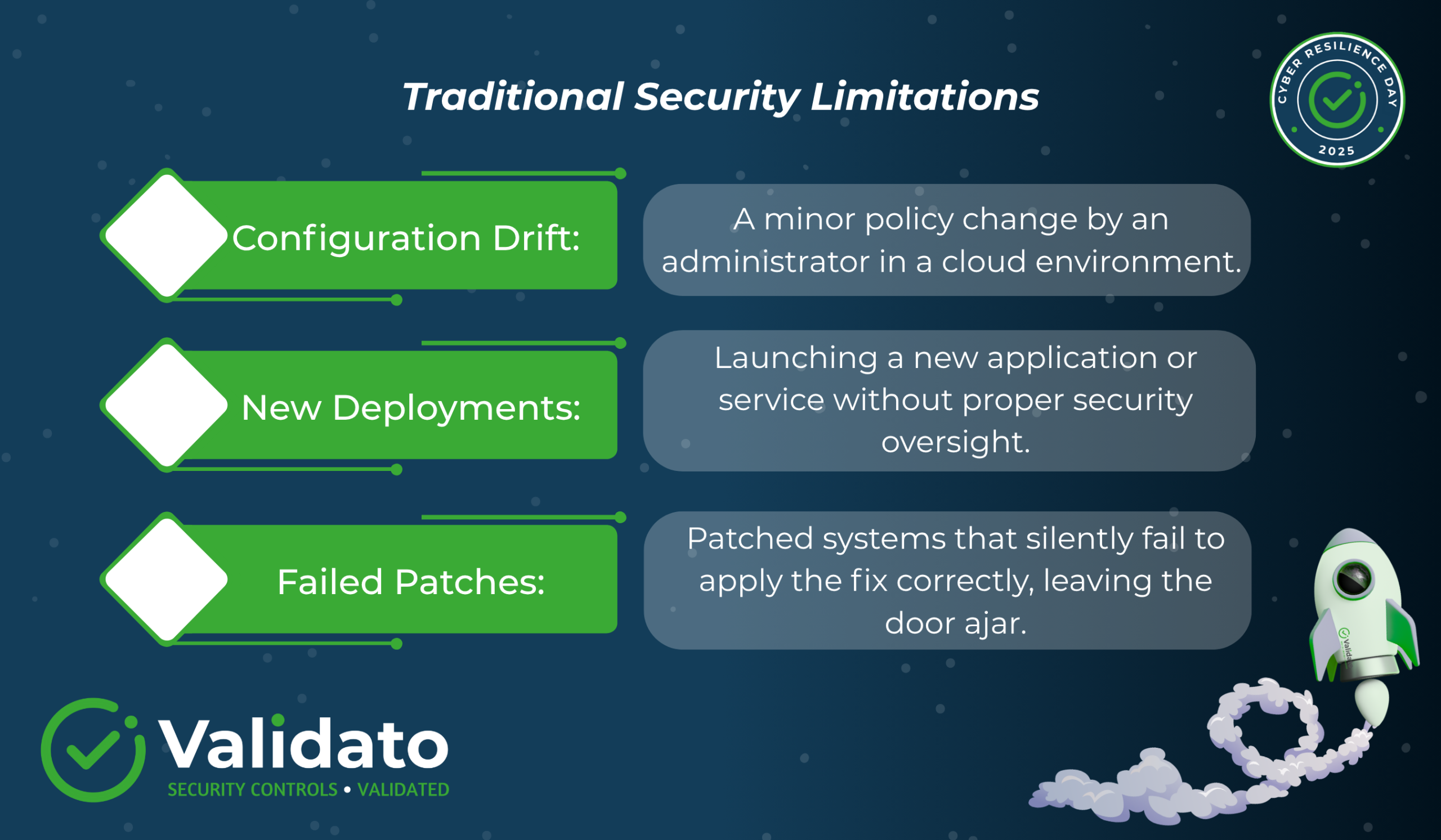
The cumulative result of this episodic testing is a perpetually uncertain security posture. Security spending is high, but the most fundamental question remains unanswered in real-time: “Are my expensive controls truly working, right now, against the threats that matter?”
The Industry Shift
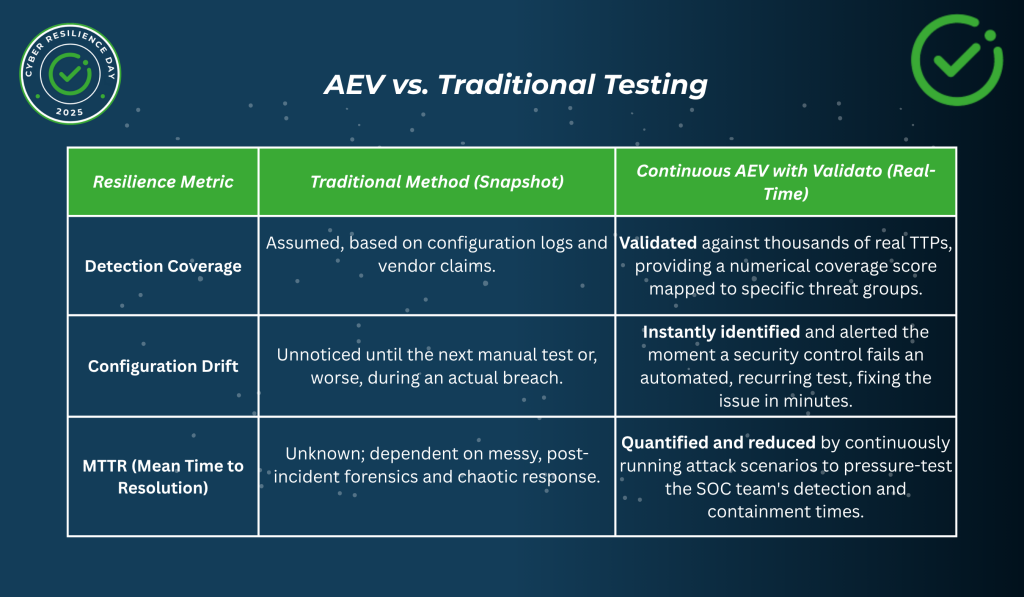
This inherent volatility and lack of continuous assurance is driving a major shift across the industry. According to the Gartner Report on Breach and Attack Simulation (BAS) adoption, “By 2027, more than 40% of enterprises will use Breach and Attack Simulation (BAS) tools to assess the efficacy of their security controls.” This statistic powerfully underscores the industry-wide recognition that traditional, manual methods fail to provide the continuous, high-fidelity assurance required for modern resilience.
AEV: The Engine of Continuous Resilience and Control Assurance
Adversarial Exposure Validation (AEV) is the technical process of continuously and safely challenging your live security environment. By simulating the tactics, techniques, and procedures (TTPs) used by real-world adversaries.
The critical difference is that the goal is not to find a vulnerability, but to validate the effectiveness and performance of an existing control. AEV turns your security stack into a measurable, data-driven entity.
As one of the world’s foremost cybersecurity agencies states, organisations must “transition from reactive security models to continuous validation to ensure their controls are effective against techniques used in the wild”. AEV is that essential transition, enabling the continuous measurement and adaptation required to meet this gold standard of cyber resilience.
Validato: Driving Cyber Resilience Through AEV
The Validato platform is purpose-built to transform Continuous AEV into an operational reality for security teams. It takes the academic theory of resilience and translates constant, safe testing into tangible, quantifiable benefits.
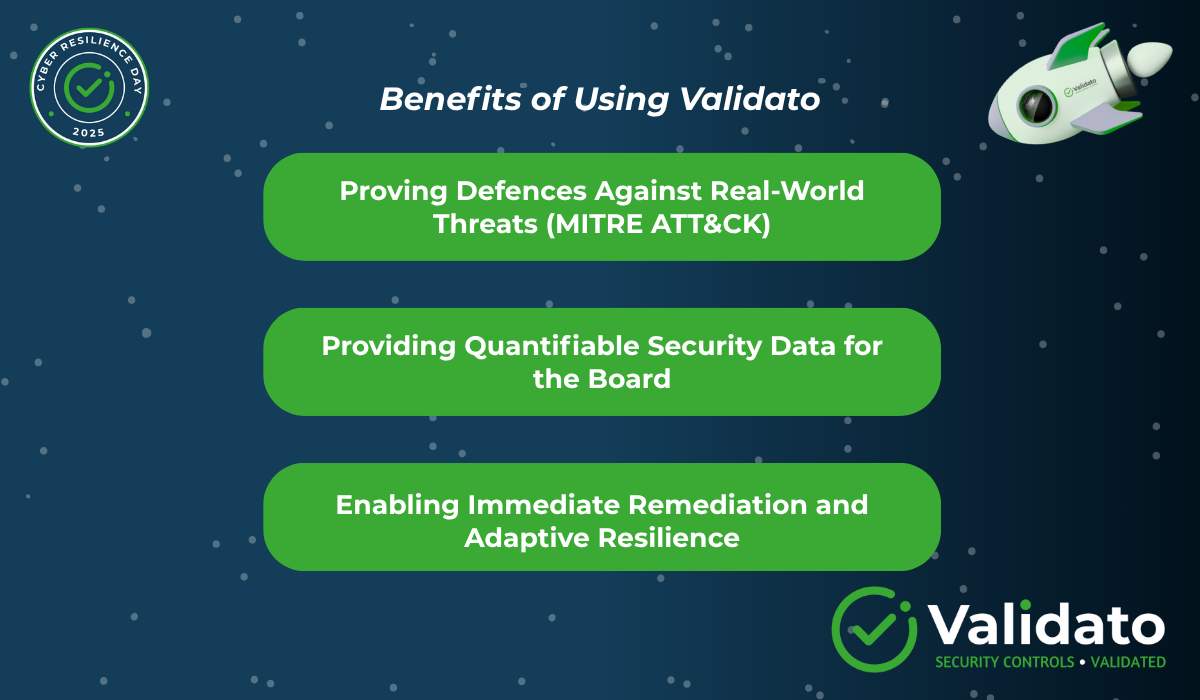
1. Proving Defences Against Real-World Threats (MITRE ATT&CK)
Attackers’ real-world tactics should drive how you test your security controls. Thats why Validato’s AEV is built entirely around the MITRE ATT&CK Framework, aligning your defence testing with known, specific adversary behaviours.
- How Validato Works: Rather than simply confirming a patch is installed, Validato executes actual post-exploitation TTPs (such as credential dumping, process injection, and lateral movement) that the original vulnerability could have enabled. Therefore, this ensures your EDR or SIEM rules are correctly configured to detect and alert on the full attack chain, proving your defences can withstand a real-world adversary, not just a checklist.
2. Providing Quantifiable Security Data for the Board
One of the biggest struggles for CISOs is effectively communicating security risk to the executive team and board. Validato solves this by providing impartial, data-driven evidence.“We have validated 92% coverage of the MITRE ATT&CK Initial Access techniques, and our average time-to-detect (TTD) for critical threats is 3 minutes.” Ultimately, this level of quantifiable, auditable data provides the confidence and the resilience assurance that executives and regulators demand.
3. Enabling Immediate Remediation and Adaptive Resilience
Configuration drift is the silent killer of security posture. A setting changed in the cloud, or an EDR policy modification, can instantly and invisibly open a critical hole.
- Validato & Adaptive Resilience: By running AEV tests continuously, Validato provides immediate feedback loops. If a test simulating a common lateral movement technique (like PsExec or WMI) suddenly succeeds where it failed yesterday, the platform alerts your team within minutes. This allows security engineers to precisely identify and fix the control. Before an attacker can exploit the newly exposed vulnerability. Therefore, this proactive control maintenance, by fixing the defence faster than the attacker can act, is the very definition of adaptive resilience
Conclusion: Achieving Continuous Cyber Resilience
In summary, the era of relying on sporadic, episodic testing is over. Achieving the gold standard of Cyber Resilience requires a commitment to continuous validation. However, by operationalising AEV through a specialised platform like Validato, organisations can confidently move past the guessing game and begin knowing the true, real-time efficacy of their multi-million dollar security stack. In fact, this is the only way to build a security program that doesn’t just block attacks, but sustains the business through them, ensuring operational continuity in the face of inevitable cyber challenges.
For more insights or tailored guidance on enhancing your security posture, connect with Validato today!


